SRTool User Page: Difference between revisions
From Yocto Project
Jump to navigationJump to search
David Reyna (talk | contribs) (User documentation for the SRTool) |
David Reyna (talk | contribs) |
||
| (7 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
This page summarizes the Security Response Tool (SRTool) user documentation. | This page summarizes the Security Response Tool (SRTool) user documentation. | ||
__FORCETOC__ | __FORCETOC__ | ||
<br/> | <br/> | ||
== Goals == | == Goals == | ||
* A common system to track and share security issues, combining community | * A common system to track and share security issues, combining community CVEs | ||
* A simple yet flexible interface for reporting and exploring the security issues | * A simple yet flexible interface for reporting and exploring the security issues | ||
* A place to upload and share attachments, including patches, fixes, emails, and documents | * A place to upload and share attachments, including patches, fixes, emails, and documents | ||
* The ability to generate accurate and up-to-date reports and exports | * The ability to generate accurate and up-to-date reports and exports | ||
** Status on a given CVE and its defects, for a specific product or for all affect products | ** Status on a given CVE and its defects, for a specific product or for all affect products | ||
** Compliance reports on sensitive | ** Compliance reports on sensitive CVEs, for example the chain of events and who-knew-what-when | ||
** Status of each product, for the related CVE defects Compliance reports on sensitive CVE's, for example the chain of events and who-knew-what-when | ** Status of each product, for the related CVE defects Compliance reports on sensitive CVE's, for example the chain of events and who-knew-what-when | ||
** Ability to easily export that data to spreadsheets and to the public CVE database | ** Ability to easily export that data to spreadsheets and to the public CVE database | ||
* The ability to securely store embargoed | * The ability to securely store embargoed CVEs and data, complete with user protection and data encryption | ||
* Tools to help manage the ongoing influx of | * Tools to help manage the ongoing influx of CVEs (around 1000 per month) so that expert time is not wasted and crucial CVE's are not lost | ||
* In general, a managed and automated tool set based on open source to replace splintered email threads and brittle manual systems | * In general, a managed and automated tool set based on open source to replace splintered email threads and brittle manual systems | ||
<br/> | <br/> | ||
== Basic | == Basic introduction to the interface == | ||
* This | * <strong>Initial data set</strong>: This initial data set contains the integrated CVE, Defect, and Sustaining data for 'CVE-2015-*' to 'CVE-2018-*' | ||
* The title bar "SRTool:Security Response Tool" will always link you back to the home page | * <strong>Home page</strong>: The title bar "SRTool:Security Response Tool" will always link you back to the home page | ||
* In tables there are three ways to adjust the data set, and they can be used separately and/or together to get the best results | * <strong>Tables</strong>: In tables there are three ways to adjust the data set, and they can be used separately and/or together to get the best results | ||
** <strong>The search bar</strong>: most of the text fields are searchable. Enter a value (like 'meltdown'), all records that have that string in those fields will appear | ** <strong>The search bar</strong>: most of the text fields are searchable. Enter a value (like 'meltdown'), all records that have that string in those fields will appear | ||
** <strong>The column sort</strong>: all column titles that appear in blue can be used to sort using that column. Click a second time to reverse the sort | ** <strong>The column sort</strong>: all column titles that appear in blue can be used to sort using that column. Click a second time to reverse the sort | ||
** <strong>The column filter</strong>: when you click on the 'cone' symbol in a column title you can select a filter based on that column's data | ** <strong>The column filter</strong>: when you click on the 'cone' symbol in a column title you can select a filter based on that column's data | ||
** At the bottom of each table you can set the page size and jump to diff pages | ** At the bottom of each table you can set the page size and jump to diff pages | ||
* The | * <strong>User Model</strong>: The SRTool uses the Django User Access Model | ||
* | |||
* | <br/> | ||
* | == SRTool Record Types == | ||
* | |||
* | === CVE Record === | ||
* | |||
** | * A CVE record is the representation of an upstream CVE that comes from MITRE, NIST, or other sources | ||
* The data in a CVE record is intended to be pristine, however you can superimpose local edits to the CVE records to fix upstream errors | |||
* You can create "local" CVEs for issues that do not yet have a formal CVE number | |||
=== Vulnerability Record === | |||
* A "Vulnerability" is a SRTool record that tracks a given issue across the orgainzation's products and releases | |||
* It normally tracks a single CVE, but it can also attach to multiple CVEs that may be duplicates or overlaps | |||
* Pertinate data like patches, reproducers, or documents can be attached and thus shared | |||
* A Vulnerability can be created without a CVE, in case the CVE does not yet exist or is currently embargoed | |||
=== Investigation Record === | |||
* An "Investigation" is a SRTool record that tracks a given Vulnerability to a specific product and defect | |||
* It normally attaches to a single defect, but it can also be attached to multiple defects in case (for example) the vulnerability is broken across several functional teams (e.g. kernel, user space, hardward, ...) | |||
* Pertinate data like patches, reproducers, or documents can be attached and thus shared | |||
* An Investigation can be created without a defect, in case the issue is still being investigated or is currently embargoed from the public defect database | |||
=== Defect Record === | |||
* A "Defect" is the representation of the organization’s defect (Jira, Bugzilla) | |||
* It connects to a CVE via the parent Investigation record and Vulnerability record | |||
=== Overview of the SRTool Records === | |||
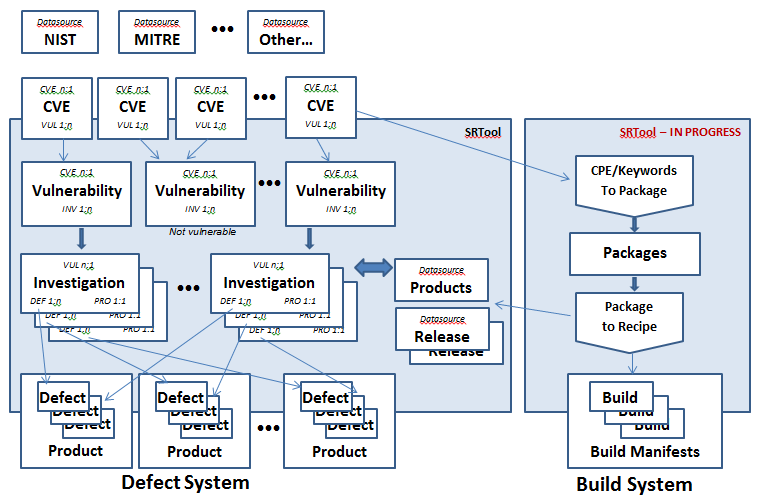
Here is a picture of the high level SRTool record structure: | |||
[[File:Records_Packages_under_SRTool.png|border|SRTool Record Structure]] | |||
<br/> | <br/> | ||
=== | == Usage Guide == | ||
=== Working with CVEs === | |||
* The CVE page is based on the NIST public page, and includes the V3 and V2 severities information, download links, and CPEs | |||
* There are tabs to see (a) the original NIST source data, (b) alternate CVE sources, and (c) SRTool edits (if added) | |||
* At the top is a place for the internal tags to help lookups and track status | |||
* At the top is a place to see the publishing state. It can include future dates, plus a "Publish Now" button | |||
* The "New CVE" link createa a new custom local CVE record | |||
* The "Fetch alt data" link adds Mitre, Debian, and other data to this CVE | |||
* The "Export" link provides CVE specific reports | |||
=== Vulnerabilities === | === Working with Vulnerabilities === | ||
* Vulnerability records track the <strong>overall status</strong> of CVE (or a group of tightly related CVEs) | |||
* Multiple related CVE's can be attached | |||
* Multiple Investigations can be attached, one per product | |||
* Comments and attachments can be added by logged-in users (for traceability) | |||
* Users can sign up for change notification emails | |||
* Vulnerabilities can be public, or locked to an invitation-only list of users | |||
* The "Edit Status ..." button allow changes to the fields like the status, priority, comments | |||
* The "Create Notification..." button is for notifying owners of status changes for the record | |||
* The "Delete" button is for deleting this record | |||
* The "Add product ..." button is for attaching a product and creating a respective Investigation record | |||
* The "New Vulnerabilities" link createa a new vulnerability record | |||
* The "Export" link provides Vulnerability specific reports | |||
=== Investigations === | === Working with Investigations === | ||
* Investigation records track the status of a CVE for a <strong>given product</strong> | |||
* Multiple defect links can be attached | |||
* Comments and attachments can be added by logged-in users | |||
* Users can sign up for change notification emails | |||
* Investigation can be public, or locked to a controlled list of users | |||
* The "Edit Status ..." button allow changes to the fields like the status, priority, comments | |||
* The "Create Notification..." button is for notifying owners of status changes for the record | |||
* The "Delete" button is for deleting this record | |||
* The "Export" link provides Investigation specific reports | |||
=== Defects === | === Working with Defects === | ||
* This table lists all of the defects being tracked by the Vulnerabilities and Investigations | |||
* A quick status overview of the defects is provided | |||
* A quick summary page per defect is provided, with a link to the actual defect | |||
=== Products === | === Working with Products === | ||
* | * The Products page shows the organization's products that are attached to the SRTool | ||
* | * Links are provided to view the product's Vulnerabilities, Investigations, and Defects | ||
=== | === Working with User Accounts === | ||
* By default you will be logged in as an anonymous "Guest" | |||
** | * Click log-in in the top bar: | ||
** | ** Select to log in with your credentials | ||
** Select to create your own Guest account | |||
* When logged in, click your user name in the top bar to: | |||
** Select to log out. This will return you to the anonymous 'Guest' account | |||
** Select to edit your account settings | |||
** Select to edit your password | |||
Latest revision as of 23:41, 24 January 2019
This page summarizes the Security Response Tool (SRTool) user documentation.
Goals
- A common system to track and share security issues, combining community CVEs
- A simple yet flexible interface for reporting and exploring the security issues
- A place to upload and share attachments, including patches, fixes, emails, and documents
- The ability to generate accurate and up-to-date reports and exports
- Status on a given CVE and its defects, for a specific product or for all affect products
- Compliance reports on sensitive CVEs, for example the chain of events and who-knew-what-when
- Status of each product, for the related CVE defects Compliance reports on sensitive CVE's, for example the chain of events and who-knew-what-when
- Ability to easily export that data to spreadsheets and to the public CVE database
- The ability to securely store embargoed CVEs and data, complete with user protection and data encryption
- Tools to help manage the ongoing influx of CVEs (around 1000 per month) so that expert time is not wasted and crucial CVE's are not lost
- In general, a managed and automated tool set based on open source to replace splintered email threads and brittle manual systems
Basic introduction to the interface
- Initial data set: This initial data set contains the integrated CVE, Defect, and Sustaining data for 'CVE-2015-*' to 'CVE-2018-*'
- Home page: The title bar "SRTool:Security Response Tool" will always link you back to the home page
- Tables: In tables there are three ways to adjust the data set, and they can be used separately and/or together to get the best results
- The search bar: most of the text fields are searchable. Enter a value (like 'meltdown'), all records that have that string in those fields will appear
- The column sort: all column titles that appear in blue can be used to sort using that column. Click a second time to reverse the sort
- The column filter: when you click on the 'cone' symbol in a column title you can select a filter based on that column's data
- At the bottom of each table you can set the page size and jump to diff pages
- User Model: The SRTool uses the Django User Access Model
SRTool Record Types
CVE Record
- A CVE record is the representation of an upstream CVE that comes from MITRE, NIST, or other sources
- The data in a CVE record is intended to be pristine, however you can superimpose local edits to the CVE records to fix upstream errors
- You can create "local" CVEs for issues that do not yet have a formal CVE number
Vulnerability Record
- A "Vulnerability" is a SRTool record that tracks a given issue across the orgainzation's products and releases
- It normally tracks a single CVE, but it can also attach to multiple CVEs that may be duplicates or overlaps
- Pertinate data like patches, reproducers, or documents can be attached and thus shared
- A Vulnerability can be created without a CVE, in case the CVE does not yet exist or is currently embargoed
Investigation Record
- An "Investigation" is a SRTool record that tracks a given Vulnerability to a specific product and defect
- It normally attaches to a single defect, but it can also be attached to multiple defects in case (for example) the vulnerability is broken across several functional teams (e.g. kernel, user space, hardward, ...)
- Pertinate data like patches, reproducers, or documents can be attached and thus shared
- An Investigation can be created without a defect, in case the issue is still being investigated or is currently embargoed from the public defect database
Defect Record
- A "Defect" is the representation of the organization’s defect (Jira, Bugzilla)
- It connects to a CVE via the parent Investigation record and Vulnerability record
Overview of the SRTool Records
Here is a picture of the high level SRTool record structure:
Usage Guide
Working with CVEs
- The CVE page is based on the NIST public page, and includes the V3 and V2 severities information, download links, and CPEs
- There are tabs to see (a) the original NIST source data, (b) alternate CVE sources, and (c) SRTool edits (if added)
- At the top is a place for the internal tags to help lookups and track status
- At the top is a place to see the publishing state. It can include future dates, plus a "Publish Now" button
- The "New CVE" link createa a new custom local CVE record
- The "Fetch alt data" link adds Mitre, Debian, and other data to this CVE
- The "Export" link provides CVE specific reports
Working with Vulnerabilities
- Vulnerability records track the overall status of CVE (or a group of tightly related CVEs)
- Multiple related CVE's can be attached
- Multiple Investigations can be attached, one per product
- Comments and attachments can be added by logged-in users (for traceability)
- Users can sign up for change notification emails
- Vulnerabilities can be public, or locked to an invitation-only list of users
- The "Edit Status ..." button allow changes to the fields like the status, priority, comments
- The "Create Notification..." button is for notifying owners of status changes for the record
- The "Delete" button is for deleting this record
- The "Add product ..." button is for attaching a product and creating a respective Investigation record
- The "New Vulnerabilities" link createa a new vulnerability record
- The "Export" link provides Vulnerability specific reports
Working with Investigations
- Investigation records track the status of a CVE for a given product
- Multiple defect links can be attached
- Comments and attachments can be added by logged-in users
- Users can sign up for change notification emails
- Investigation can be public, or locked to a controlled list of users
- The "Edit Status ..." button allow changes to the fields like the status, priority, comments
- The "Create Notification..." button is for notifying owners of status changes for the record
- The "Delete" button is for deleting this record
- The "Export" link provides Investigation specific reports
Working with Defects
- This table lists all of the defects being tracked by the Vulnerabilities and Investigations
- A quick status overview of the defects is provided
- A quick summary page per defect is provided, with a link to the actual defect
Working with Products
- The Products page shows the organization's products that are attached to the SRTool
- Links are provided to view the product's Vulnerabilities, Investigations, and Defects
Working with User Accounts
- By default you will be logged in as an anonymous "Guest"
- Click log-in in the top bar:
- Select to log in with your credentials
- Select to create your own Guest account
- When logged in, click your user name in the top bar to:
- Select to log out. This will return you to the anonymous 'Guest' account
- Select to edit your account settings
- Select to edit your password